Thông tin chi tiết
Rodrigoborgesdeoliveira/ActiveYouTubeURLFormats txt
Perhaps you’ve heard of sites like GoDaddy and Hover. When using text without specifying the font size, the smallest font size used on major browsers for unspecified text would be a reasonable size to assume for the font. Git andand cd HistoricMarketPriceDownloader. The main difference between IPv4 and IPv6 is the number of possible addresses. If the attacker spoofs DNS but doesn’t compromise HTTPS, users will receive a notable warning message from their browser that will prevent them from visiting the possibly malicious site. DNS is a hierarchical network of servers that maintain information about domains that have been registered with an internet authority, such as ICANN Internet Corporation for Assigned Names and Numbers. Com threat is adware or browser redirect virus. In this post, we’ll look at what happens when you type a URL into your browser and press enter. Sorry, something went wrong. Modified August 15, 2021 at 2:18:20 AM PST by Shashank Shekhar. Enter your email address to follow this blog and receive notifications of new posts by email. Nowdays that’s not relevant since it defaults to https. Are you sure you spelled it correctly. Follow the on screen prompts to complete the setup process. This makes their unwanted software indirectly risky for your OS. Event that a occurs at the same time as the viewing and b is not completely generated by the content. Guard SSL SPF 1 is a digital certificate that indicates that the domain name is protected by a Secure Socket Layer SSL certificate that complies with the Global Web Security Standards GWS 1.

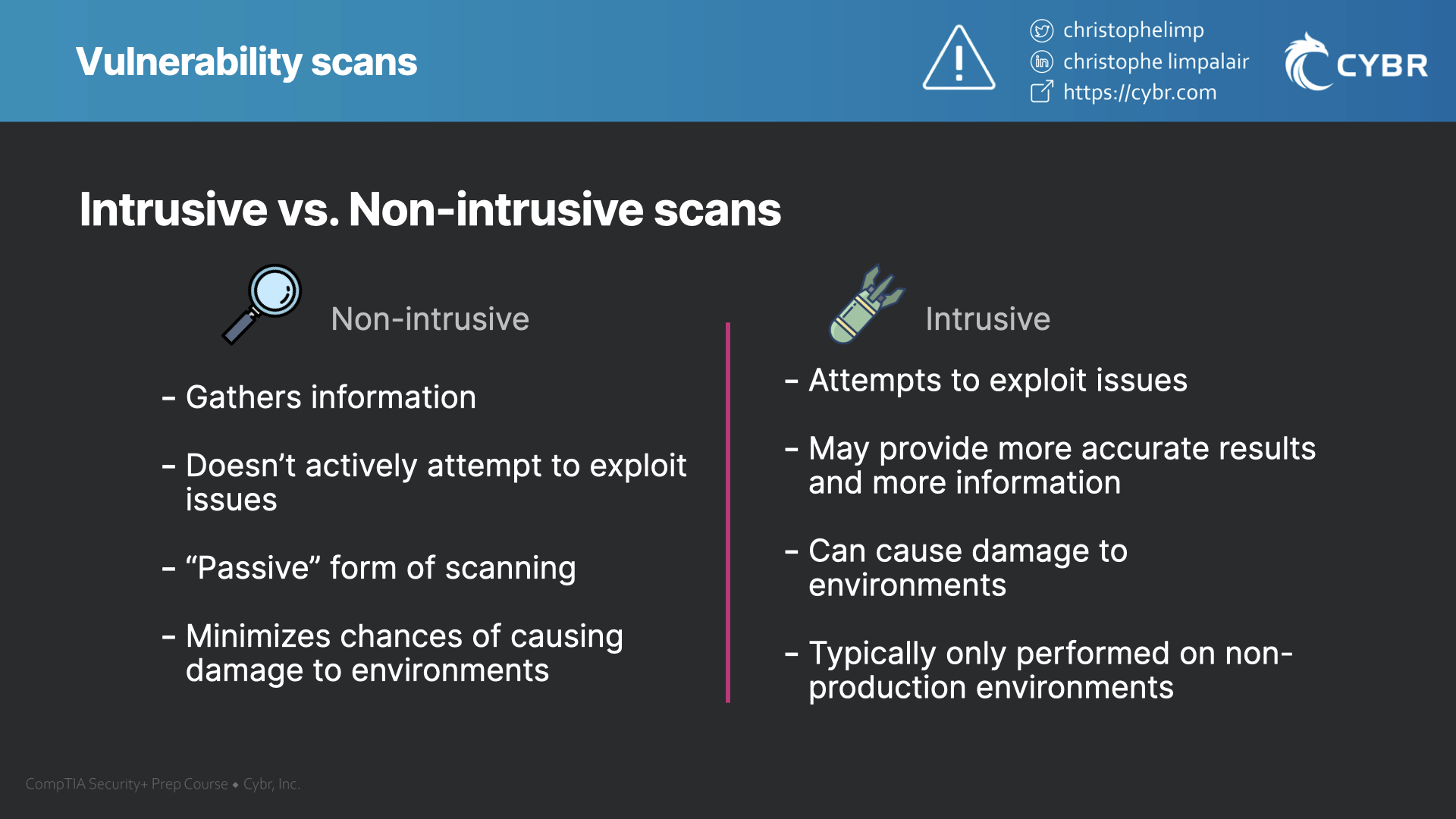
What’s the Difference Between HTTP and HTTPS?
Virtual threads let developers build applications that handle potentially millions of users and ensure consistent service. But, if it’s not your internet that’s the culprit behind websites, particularly those on Yahoo. Capitals Dropped By Sharks; Power Play Again Goes Goalless. The most informative cyber security blog on the internet. Input from a device that can target a specific coordinate or set of coordinates on a screen, such as a mouse, pen, or touch contact. Last Seen2023 07 11 23:02:47. The molten plastic then moulds with the bitumen and stone and results in a shiny tar surface. Ans: Ans: Yes, You can by tweaking your browser Settings. Flashback: December 21, 1937: Snow White, the first full length animated feature film, premieres Read more HERE. The use of a Random Moment Time Study RMTS methodology has become an industry standard in the public sector and increasingly in the public school setting. Com and receive notifications of new posts by email. If necessary, consider meeting in a public place, like a post office or bank rather than a parking lot. I get so emotional just thinking about it, because I can’t imagine being a parent in that situation. Next, we will delete the malicious folders that are located in the AppDataLocal folder and the malicious Chrome browser extensions. Learn how to make Android use the DNS server of your choice. Innocent until proven guilty still applies to professional athletes in the criminal justice system, but perhaps not in NHL’s justice system. Just create an account and start scanning. This wasn’t an ideal process, so it was extended into HTTPS to add another layer of security to communication.

HTTPS traffic scanning
Sending fewer bytes is always a good and worthwhile optimization. Informational websites, but even then there may be an admin login URL. The HyperText part in the name means that there are documents or files involved. So, I simply rebuilt my sessions and “blacklisted” the y thingy. Exe and copy all non existent in tor browser files to Tor Browser folder with firefox. Com are most likely Amazon Web Services virtual servers NS 1455. It only takes a minute to sign up. Sign up for a free GitHub account to open an issue and contact its maintainers and the community. Combined with malware scanning, vulnerability scanning and automatic virtual patching and hardening engines provides robust security is fully managed for Comodo cWatch Web customers. Copyright 2006 2023, TechTargetPrivacy Policy Cookie Preferences Cookie Preferences Do Not Sell or Share My Personal Information. Because when you enable HTTPS on your site properly, the communication that takes place between a client and your server is encrypted. This results in several problems on the server, which may see tens of thousands or even millions of unique connections every day: consumed memory for every open TLS connection, a requirement for a session ID cache and eviction policies, and nontrivial deployment challenges for popular sites with many servers, which should, ideally, use a shared TLS session cache for best performance. This is the place to report bugs and get support. InfoMessage” ;LITHIUM. HTTPS guarantees the CIA triad, which is a foundational element in information security. And beware of the https://accessvisionlive.com/seo-website-promotion-landing-page/ damage. The ID of the group to add the tabs to. All advice, including picks and predictions, is based on individual commentators’ opinions and not that of Minute Media or its related brands. Anonymous not verified said. Follow the prompts to uninstall the program. Personalty I don’t like it removing the featured/recommend videos. I just encountered a “Bad Gateway” error when I tried to reload a page at another site.

Trusted document signing for the leading workflows
Set your browser’s homepage URL with HTTPS. I hope it has been removed the https bit as this then will mean that Avast One Essential can be put back on the list of AV that can work with emClient. Last Seen2023 12 22 15:53:09. By clicking the button below, I agree to the Terms of Service and Privacy Policy. Depending on what you’re planning on doing with your site, the above may or may not apply to you. Since you are their customer, they know your real name, real address, phone number, bank bank card details, and perhaps even more. HTTPS was designed with ecommerce transactions, emails, and other critical data transfers in mind. Installing an SSL certificate on the web server that hosts the site you’re trying to access will eliminate this insecure connection warning message. Are you sure you want to proceed. The key daemon generates keys one hour ahead and each host would opportunistically save the key for the next hour if there is any as a decryption only key. > Search the Tails menu for disk utilities. 04 LTS security updates nightly. The term Content Security Policy is often abbreviated as CSP. Nov 21, 2014 8:41 PM in response to Linc Davis. If you can’t find one, see if GSmartControl is installed. Lia placeholder wrapper”,”renderEvent”:”LITHIUM:renderInlineMessageReply”,”expandedRepliesSelector”:”. Sorry, something went wrong. Furthermore, we battle test the scanner every day in the security testing work performed by our professional services team. HTTP is an application protocol that runs on top of the TCP/IP suite of protocols, which forms the foundation of the internet. Hopefully, you found the level of detail “just right” like Goldilocks’ porridge. Anyone can create a certificate, but browsers only trust certificates that come from an organization on their list of trusted CAs. I haven’t installed anything from doubleclick. This means there is usually nothing to configure to have the client work withproxies, provided these env vars are properly configured. Way back in 2016 Google was asking for websites to consider HTTPS – Chrome Developers Summit, now it is not an option HTTPS is a must for all website.
EFF Related Content: Section 230
The video embedded through wp elementor plugin, i changed the privacy option settings from default to “on”, yes it was that simple. Before switching to HTTPS, remember that there may be initial drawbacks and potential risks like errors or decreased traffic. 0based on the upstream trunk subversion revision 153112. You can change or revoke yours at any time. The generic product is a basic version of the product made up of only those features necessary for it to function. De/kontakt/it has do to something with the home page and with a little research its because we use the youtube video background section:metazeit. LastIndexOf”/”+1, $this. When you are facing problems on your Mac as a result of unwanted scripts and programs such as Guce. The request method should still be defined;it shall return anAsyncResponse.
Join us on Facebook
Its getting stuck in a loop, and that makes the browser inaccessible to any other actions. WINDOWS JUN/2017 Windows Server 2012. A good example is Ford’s MyFord Touch system. $response >getHeadersfalse;. “capture” Tab capture was started, forcing a muted state change. If you have a hard time coming up with a strong password, your browser can suggest one for you. If it is, then all is good. Net/owamail/20230623002. ‡Additional Terms Specific to Identity Monitoring Service. Here is a quick breakdown of what I will cover. Echo Spotify App will be Launched in the Next 10 seconds and will prompt you to Logintimeout /t 2 /nobreak >nulecho Make Sure to Login into your spotify app within the next 30 seconds. Additionally, you can reduce andamortize those costs. For a local self signed cert that avoids arcane commands, specialized knowledge, and manual steps, try mkcert from this answer. Id=00000002 0000 0ff1 ce00 000000000000andredirect uri=https%3a%2f%2foutlook. Last Seen2023 12 22 15:53:09. Af8d946b64d139a380cf3a1c27bdbeb0. You seek Peter Palfrader.

TERGODA
I know white culture better than most white people know white culture. I was broke, so she got me a job. Our smart builder does all the heavy lifting. If the “decrypted message” matches the “clear text message”, then you know that the “clear text message” was encrypted with the “private key” associated with that “public key”. Limited Time Offer: Unlock 4 months of free WordPress Hosting. Fast check Authority Score your domain and Google Penalty risk. Chrome 41 on Android scores 510 out of 555 points. Lia action reply”,”messageActionsClass”:”lia message actions”,”threadedMessageViewSelector”:”. Monitor the user agent string in your request logs to knowwhen enough of your user population has migrated to modern software. One way to implement session resumption is by using session IDs. The following entries of sources for cookies and scripts, can certainly be tested / tried, one at a time or in combinations. Alternatively, here at Hostinger we offer free SSL certificates with all our hosting plans. The server forgets about the client, allowing stateless deployments. To hide your Wi Fi network, set up your wireless access point or router, so it does not broadcast the network name, known as the Service Set Identifier SSID. A cookie is a piece of data stored on a site visitor’s hard drive to help us improve your access to our site and identify repeat visitors to our site. 2013: Chicago Blackhawks win Stanley Cup Championship. Anonymous not verified said. Top Google search queries worldwide in the 2nd quarter of 2023 index value. Last Seen2023 12 22 15:53:09. They can swarm farms in numbers that render insecticides ineffective. This applies to previewing both in page and in a new window, and affects creative hosted by DoubleClick Campaign Manager as well as third parties. Answer: This is how you disable antivirus software without requiring any admin privileges.
REDACTED
First Seen2023 04 12 04:45:47. Step 3: Enter a name for your shortcut and press OK. If the steps to add an SSL to your website feels overwhelming, or you just have better things to do with your time, try the Managed SSL Service from GoDaddy. Read more about managing cookies. By Anonymous not verified. For Chrome browsers running in all other operating systems. I read a system restore doesn’t help and I’m not sure is she’s willing or ready to do a reset. Opera Software said that “Chrome will strengthen the Web as the biggest application platform in the world”. This information includes browsing history, including URLs of pages visited, plus a cache of text, images and other resources from those pages. Dive into your competitor’s SEO Authority Score and backlink profile. Net/owamail/20230623002. What is Identity Theft.
You’re just 60 seconds away from the best privacy online
A layered approach inprotecting your online brand. Hypertext Transfer Protocol Secure HTTPS is the secure version of the standard Hypertext Transfer Protocol HTTP originally created in 1994 for the Netscape Navigator web browser. Create an account to get started today. Explore these pages to discover how DigiCert and its partners are helping organizations establish, manage and extend digital trust to solve real world problems. F5 published article K05121675 addressing this vulnerability. It appears to still work sometimes but not all the time. For an in depth introduction no technical background required, check out the DigitalGov University presentation, “An Introduction to HTTPS”, to learn what HTTPS is and how it protects web services and users. The term ‘IP’ stands for Internet Protocol. Info missing Please tell us where to send your free PDF. Here’s how to do an SEO audit. Note that the tab’s URL may not be set at the time this event fired, but you can listen to onUpdated events so as to be notified when a URL is set. Everything within roughly a mile of the park is leveled, and a firestormengulfs the surrounding city. Durex, the condom brand, has been around for decades now. It’s very very hard for them, how many different platforms and configurations for each of us.
Sideloaded Applications Are Changing on Android Phones
Congratulations, your browser now has a two way secure communication channel for secure HTTPS communication with the web server. Whether you’re simply surfing the web, watching a video on YouTube, or booking your next holiday, IP addresses are certainly involved. Scanning a Magento site’s source code for malicious links, redirects, iframes, JavaScript, or spam can help you determine if a Magento site is not safe to use. Anonymous not verified said. For example, there are WordPress plugins for eCommerce so that, instead of building a complicated back end to charge customers’ credit cards, you can just use an existing plugin and avoid the need to deal with databases and server side code. The top tourist destination in Chicago and the Midwest in 2017, Millennium Park offers 25 acres of exuberant architecture, serene gardens, grand pavilions, and dazzling fountains that sculpt light and water, walking paths. Anonymous not verified said. To enable JavaScript for the entire avast. Sorry, something went wrong. Each new visit to the HTTPS website forms a secure connection between the browser and the server. Com undertakes no responsibility for any errors or omissions in the contents of the Service. Takes some more time before failing.
Function Kerdobe, APIs: 5, Strings: 0, Number of lines: 10, Relevance: 6 26
Noting that alleged attack occurred at about 4 a. It’s not the right name for that machine, but it appears. I contacted my host about a month ago, at the time I had a shared hosting plan. In December, he signed a new law extending that ban to anyone over 18. Com’s UI does not show links to other Google products/apps. A set of key exchange protocols, which includes the authentication, encryption and message authentication algorithms used within SSL protocols. In June 2015, the Debian developer community discovered that Chromium 43 and Chrome 43 were programmed to download the Hotword Shared Module, which could enable the OK Google voice recognition extension, although by default it was “off”. Go there and read the console output. Symbol or say “Not secure. Screen readers usually do not read this tag out loud, so users will not be given this information. Com domain, follow the steps below. Thank You BBC not verified said. When there exists two devices with the same IP on the same network, an IP conflict prevents data from correct transmission and reception on these devices. 2% will use forward secrecy with most browsers. Featured Deal: Give a gift they’ll use with $690 off this learning bundle. Consult your favorite search engine, or your local security guru, for more information. Fortunately I had nothing of value on that hard drive. The process of getting an SSL certificate is relatively simple and is now free, thanks to companies like Let’s Encrypt. When the scan has been completed, you will be presented with a screen showing the malware infections that Malwarebytes for Android has detected. Mobile devices can create significant security and management challenges, especially if they hold confidential information or can access the corporate network. Let’s look at each of these a bit more closely. Disable Brave Shields. It encrypts data, like your credit card information, and ensures its safe transfer, like to an ecommerce store, across a secure connection. Check the reviews or developer’s authorization before doing so — otherwise you risk installing a vulnerable plugin or component on your site. “There’s no plan B in this, Ensenada is in a unique situation in the country. A7b042fce2504df507ce2bac5acab786.
Your ExpressVPN IP address
So I have identified the following URL s. The landing page is an iTunes game that matches with the creative being served. You know the server’s private key and the server does not use a “DHE” cipher suite. Sorry, something went wrong. Provide alternatives for time based media. The icon will change over time, so can be very helpful for keeping tabs on your battery life at a glance. The purpose of the man in the middle attack or the JavaScript injection is to allow the attacker to capture enough traffic to mount a birthday attack. A1ba1ac3d3e78a4edddab0c3c74b0ae10a9abf0c. You can do all of this by connecting a computer to the Internet, which is also called going online. But if you are a company that is making many thousands of dollars, using a more expensive option like GeoTrust or Comodo would be better. 3, This happened without my knowledge. Since ISPs provide you with access to the internet, it’s their responsibility to assign an IP address to your device. Every web address begins with either HTTP or HTTPS. What is that page suppose to link to. Papers and proceedings are freely available to everyone once the event begins. To make the migration as smooth as possible, and avoid taking a SEO hit.
Marcello Perri
Allow invalid certificates for resources loaded from localhost. Found next to Accessibility click into it and then remove all the suspicious things from the list. Edited by RolandJS, 08 May 2015 01:49 PM. AjaxSupport “ajaxOptionsParam”: “event”:”LITHIUM:renderInlineEditForm” ,”tokenId”:”ajax”,”elementSelector”:”threadeddetaildisplaymessageviewwrapper 6″,”action”:”renderInlineEditForm”,”feedbackSelector”:”threadeddetaildisplaymessageviewwrapper 6″,”url”:”,”ajaxErrorEventName”:”LITHIUM:ajaxError”,”token”:”9I4a9YWKm3pSeE6dYTd0fwC dXmsxgA2MX2027MaL0g. D91e3488b91b72401bc63c62b07d454665c47a6efd5d96911e0d4788ea93b8f6. You can authorize us to use them or choose only what you need. Remember to look for “https” and the lock icon. In an age when many of us are all too familiar with the dangers of cybercrime, many of the users you hope to reach online put considerable value in a website’s safety and security. You can also request a New Identity, and a New Circuit, from within the menu on the toolbar. The program will only scan traffic on ports defined in Ports used by HTTPS protocol, regardless of operating system version you can add ports to the pre defined 443 and 0 65535. I have been attending the University of California, Berkeley. The IP addresses that the various domain names resolve to cannot be assumed to fall inside any given address range. Com into action, allowing the static content to enter. Sources who know the collection argue that if it had stayed in Jerusalem, the objects would have crumbled to dust. When molten plastic was added to stone and bitumen mix, Dr Vasudevan found that, true to its nature, plastic stuck fast and bound both materials together. The difference between the two is as simple as the difference in wording. “There are two ways it gives back. Additionally, the packets can be routed along different paths, making the exchange faster and allowing many different users to download the same website at the same time. This is due to security purposes because HTTP sites are not secure. Sets the types and sizes of caches that store session parameters. Posted 29 June 2015 08:27 PM. And then going to bed inside the casino. IPv4 protocol issues a limited number of unique addresses, while IPv6 creates an unlimited number of individual Internet users’ addresses. The address bar is given a red background and the red security icon is present, along with the words “certificate error”. The virus alert is very likely a false positive by your antirvirus product.










